My WordPress hacked by c99madshell script
After all the excitement of last Friday’s attempted hack on my travelblog, and the subsequent upgrade to WordPress 2.6 – I thought everything was under control. Boy was I wrong!
A few hours ago I received a blog comment (from a Mr Andrew Wong) on the travelblog:
http://www.lee-and-lucy.com/travelblog/index.php?p=5817
check this out!!
I clicked the link, my jaw dropped! It wasn’t an attempted hack, it was a very successful hack… I felt violated -in a digital sense. The threat was far from over!
From looking through the WordPress management screens, I couldn’t find a blog post with the ID #5817. I opened up phpMyAdmin to see if it was in the database; nope, nada, nothing!
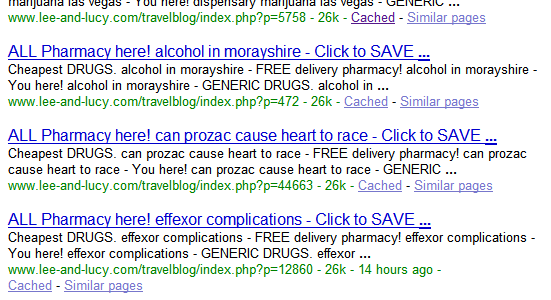
I wanted to see the extend of the problem, so I googled “site:lee-and-lucy.com“, and found a “lot” of pages… oh yes, LOTS OF SPAM!
To say the least, I was furious! I wanted to; a. resolve this asap; b. find out how this happened; c. cause pain to this would-be hacker! Obviously, option c. goes against my good karma nature, but they digitally violated my site; sticking spam in places that spam should never go!!! Furious I tell you!
Digging through my WordPress files, I find a PHP script in my theme folder called “simple.php“; it contains a nested “eval(gzinflate(base64_encode()))” string. Very suspect. I try to manually decrypt the string, (replacing the eval with an echo), but it’s nested a few levels deep… so I found a snippet of code that would easily decode/decrypt it.
The script turned out to be a modified version of c99madshell, specifically focused on WordPress hi-jacks. The script tries to inject a small trojan code into one of the core WP files (for me it was the “wp-blog-header.php“). I removed the hi-jacked code, along with the “simple.php” file (from my theme folder) – then re-upgraded to the latest WordPress (2.6) … just to overwrite any other tampered files.
Hopefully this should be the end of this matter (until next time) …. I’ll be keeping a careful eye on my WordPress installations now on.